1. –ď–Ķ–Ĺ–Ķ—Ä–ł—Ä—É–Ķ–ľ —Ā–Ķ—Ä—ā–ł—Ą–ł–ļ–į—ā—č
–Ē–ĺ–Ī–į–≤–Ľ—Ź–Ķ–ľ —Ā–Ķ–ļ—Ü–ł–ł –ĺ—ā–≤–Ķ—á–į—é—Č–ł–Ķ –∑–į TLS
ee /usr/local/etc/postfix/main.cf
# TLS smtpd_use_tls = yes smtpd_tls_security_level = may smtpd_tls_auth_only = yes smtpd_tls_key_file = /usr/local/etc/postfix/device.key smtpd_tls_cert_file = /usr/local/etc/postfix/device.crt smtpd_tls_CAfile = /usr/local/etc/postfix/rootCA.pem smtpd_tls_loglevel = 1 smtpd_tls_received_header = yes smtpd_tls_session_cache_timeout = 3600s tls_random_source = dev:/dev/urandom # A—É—ā–Ķ–Ĺ—ā–ł—Ą–ł–ļ–į—Ü–ł—Ź¬†SMTP smtpd_sasl_auth_enable = yes smtpd_sasl_exceptions_networks = $mynetworks smtpd_sasl_security_options = noanonymous broken_sasl_auth_clients = yes smtpd_sasl_type = dovecot smtpd_sasl_path = private/auth
–Ē–į–Ľ–Ķ–Ķ, –ĺ—Ā–Ĺ–ĺ–≤—č–≤–į—Ź—Ā—Ć –Ĺ–į —Ä–Ķ–ļ–ĺ–ľ–Ķ–Ĺ–ī–į—Ü–ł—Ź—Ö mozilla, –ī–Ķ–Ľ–į–Ķ–ľ —ā–į–ļ – –≤ —Ā–Ķ–ļ—Ü–ł–ł TLS –ī–ĺ–Ņ–ł—Ā—č–≤–į–Ķ–ľ
main.cf:
smtp_tls_mandatory_ciphers = high smtp_tls_mandatory_protocols=!SSLv2,!SSLv3 tls_high_cipherlist = ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!3DES:!MD5:!PSK smtpd_tls_mandatory_ciphers = high smtpd_tls_mandatory_protocols=!SSLv2,!SSLv3
—ā–į–ļ –ľ—č –Ķ—Č–Ķ –ĺ—Ā—ā–į–≤–Ľ—Ź–Ķ–ľ —Ā–į–ľ—č–Ķ –Ĺ–į–ī–Ķ–∂–Ĺ—č–Ķ, –Ĺ–į —Ā–Ķ–≥–ĺ–ī–Ĺ—Ź, –į–Ľ–≥–ĺ—Ä–ł—ā–ľ—č.
–Ē–į–Ľ–Ķ–Ķ, —Ä–į—Ā–ļ–ĺ–ľ–Ķ–Ĺ—ā–ł—Ä—É–Ķ–ľ –≤ /usr/local/etc/postfix/master.cf¬†—Ā–Ķ–ļ—Ü–ł—é —Ā sabmission
## Open 587 port for STARTTLS
submission inet n - n - - smtpd
-o syslog_name=postfix/submission
-o smtpd_tls_security_level=encrypt
-o smtpd_sasl_auth_enable=yes
# -o smtpd_tls_auth_only=yes
-o smtpd_reject_unlisted_recipient=no
# -o smtpd_client_restrictions=$mua_client_restrictions
# -o smtpd_helo_restrictions=$mua_helo_restrictions
# -o smtpd_sender_restrictions=$mua_sender_restrictions
# -o smtpd_recipient_restrictions=
-o smtpd_relay_restrictions=permit_sasl_authenticated,reject
-o milter_macro_daemon_name=ORIGINATING
## Open 465 port for SSL/TLS
smtps inet n - n - - smtpd
-o syslog_name=postfix/smtps
-o smtpd_tls_wrappermode=yes
-o smtpd_sasl_auth_enable=yes
–Ē–Ľ—Ź Dovecot –ī–ĺ–Ņ–ł—Ā—č–≤–į–Ķ–ľ –≤ dovecot.conf
# SSL (–Ķ—Ā–Ľ–ł –Ĺ–Ķ—ā —ā–ĺ ="NO") disable_plaintext_auth = yes ssl = yes ssl_cert = </usr/local/etc/postfix/device.crt ssl_key = </usr/local/etc/postfix/device.key ## Disable SSLV3 - Poodle ssl_protocols = !SSLv2 !SSLv3 ##
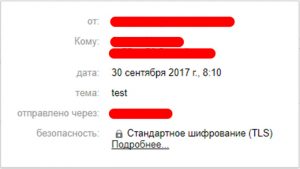
–í –ł—ā–ĺ–≥–Ķ –Ņ—Ä–ł –Ņ—Ä–ĺ—Ā–ľ–ĺ—ā—Ä–Ķ –ł—Ā—Ö–ĺ–ī–Ĺ–ł–ļ–į –Ņ–ł—Ā—Ć–ľ–į –≤ GMAIL –∑–į–≥–ĺ–Ľ–ĺ–≤–ĺ–ļ —ā–į–ļ–ĺ–Ļ:
Received: from smtp.279.ru (smtp.279.ru. [77.220.185.16]) by mx.google.com with ESMTP id o79si14839747lfi.52.2016.02.15.04.15.43 for <deryabinsergey@gmail.com>; Mon, 15 Feb 2016 04:15:43 -0800 (PST)
—Ā—ā–į–Ĺ–ĺ–≤–ł—ā—Ā—Ź –≤–ĺ—ā —ā–į–ļ–ł–ľ:
Received: from smtp.279.ru (smtp.279.ru. [77.220.185.16]) by mx.google.com with ESMTPS id d124si14810044lfg.170.2016.02.15.04.20.45 for <deryabinsergey@gmail.com> (version=TLS1_2 cipher=ECDHE-RSA-AES128-GCM-SHA256 bits=128/128); Mon, 15 Feb 2016 04:20:45 -0800 (PST)
–ė –Ņ–ĺ—Ź–≤–Ľ—Ź–Ķ—ā—Ā—Ź –∑–į–ľ–ĺ—á–Ķ–ļ –≤ —Ā–Ķ–ļ—Ü–ł–ł –Ī–Ķ–∑–ĺ–Ņ–į—Ā–Ĺ–ĺ—Ā—ā—Ć